Failover Server and Administration
Failover Server
Fault tolerance in distributed video management systems
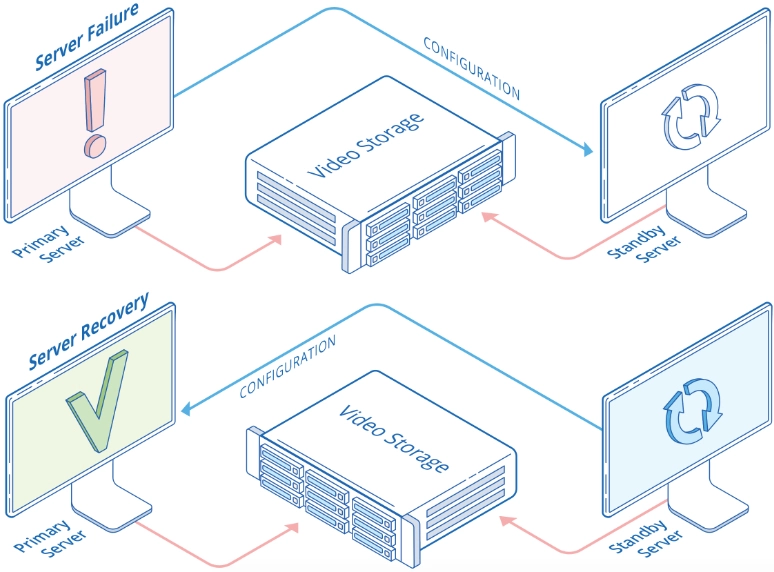
In the event of primary server communication loss, our failover system swiftly transitions operations to a standby server. This seamless transition ensures uninterrupted live video streaming and recording. The standby server takes over all functions, resuming operations without delay. Moreover, you can easily suspend any server in the cluster for maintenance, ensuring continuous video management system operation.
System Update
Your VMS software is always up-to-date
Silent Server Updates
Updating servers within a cluster is now effortless. Choose the necessary distribution provided in a .zip archive or specify a web link, and the servers will update silently. Our process ensures your video management system stays current and efficient, enhancing overall performance.
Automatic Client Update
When your Axxon One client connects to a server with a newer version of our VMS, a prompt for client software update appears. Upon confirmation, the update process begins automatically, ensuring all clients have the latest features and security tools.
Advanced User Rights Management
Streamlined administration of large systems
The new release of Axxon One is designed to elevate your security management experience. With default rights, you can configure camera access rights across all user roles, ensuring streamlined permissions as cameras are connected. Simplify your control further with camera group rights, enabling the swift assignment of access privileges to entire camera groups for specific user roles. Embracing flexibility, users can now have multiple roles simultaneously, tailoring their engagements to precise operational needs.
LDAP Authentication
Integrate with existing enterprise network services
This feature makes it possible to deduplicate user administration tasks for sysadmins at large companies. The sysadmin connects an LDAP directory to Axxon One and selects which users to add. After this, operators can log in to the video management system by entering their domain credentials. The administrator can also associate VMS access rights with corporate directory groups. When a user profile is deleted on the LDAP server, it can be automatically deleted in Axxon One.
Related Resources
Explore the comprehensive technical specifications of Axxon One VMS software, including core functions, special features, video analytics, and supported devices and standards.
Download the PDF version of the complete Axxon One presentation, containing detailed information about our advanced video management software.
Access general information about Axxon One VMS features and technologies in a convenient form.